draft is finished, still missing good dns registry reference
This commit is contained in:
parent
83ae4d53bc
commit
833752661a
@ -1,4 +1,4 @@
|
|||||||
Title: Getting Started: Installing webserver software and publishing your website
|
Title: Installing webserver software and publishing your website
|
||||||
Date: 2019-01-14
|
Date: 2019-01-14
|
||||||
Category: fundamentals
|
Category: fundamentals
|
||||||
Tags: server, router, introduction, lan, wan
|
Tags: server, router, introduction, lan, wan
|
||||||
@ -8,6 +8,7 @@ Author: hbsc & friends
|
|||||||
Status: published
|
Status: published
|
||||||
|
|
||||||
# SUPER UNDER CONSTRUCTION
|
# SUPER UNDER CONSTRUCTION
|
||||||
|
TODO: add good dns registry reference
|
||||||
|
|
||||||
##Introduction
|
##Introduction
|
||||||
|
|
||||||
@ -22,7 +23,7 @@ The instructions on this guide were run on a Debian Stretch distribution.
|
|||||||
|
|
||||||
- A spare computer.
|
- A spare computer.
|
||||||
- A basic understanding of the command line.
|
- A basic understanding of the command line.
|
||||||
- An [ssh server and client](ssh.html) installed
|
- An [ssh server and client](demystifying-ssh.html) installed
|
||||||
- A registered domain name
|
- A registered domain name
|
||||||
- Have an available power socket next to your router.
|
- Have an available power socket next to your router.
|
||||||
- An ethernet cable to connect your server to the router.
|
- An ethernet cable to connect your server to the router.
|
||||||
@ -140,8 +141,8 @@ ServerAdmin webmaster@localhost
|
|||||||
# modules, e.g.
|
# modules, e.g.
|
||||||
#LogLevel info ssl:warn
|
#LogLevel info ssl:warn
|
||||||
|
|
||||||
ErrorLog ${APACHE_LOG_DIR}/error.log
|
ErrorLog ${APACHE_LOG_DIR}/mydomain.error.log
|
||||||
CustomLog ${APACHE_LOG_DIR}/access.log combined
|
CustomLog ${APACHE_LOG_DIR}/mydomain.access.log combined
|
||||||
|
|
||||||
# For most configuration files from conf-available/, which are
|
# For most configuration files from conf-available/, which are
|
||||||
# enabled or disabled at a global level, it is possible to
|
# enabled or disabled at a global level, it is possible to
|
||||||
@ -157,9 +158,15 @@ Enable this configuration by running:
|
|||||||
$ sudo a2ensite mydomain.org
|
$ sudo a2ensite mydomain.org
|
||||||
```
|
```
|
||||||
|
|
||||||
|
Restart Apache to load the new configuration:
|
||||||
|
|
||||||
|
```bash
|
||||||
|
$ sudo service apache2 restart
|
||||||
|
```
|
||||||
|
|
||||||
## HTTPS
|
## HTTPS
|
||||||
|
|
||||||
HTTPS, which stands for *hypertext transfer protocol secure*, is an extension of the HTTP protocol. As its name suggests, it adds a layer of security to the data exchanged between client and server. By adding an encryption layer to the exchanged packets, it seeks to avoid man-in-the-middle attacks, eavesdropping, etc.
|
HTTPS, which stands for *hypertext transfer protocol secure*, is an extension of the HTTP protocol. As its name suggests, it adds a layer of security to the data exchanged between client and server. By adding an encryption layer to the exchanged packets, it seeks to avoid man-in-the-middle attacks, eavesdropping, etc. While HTTP uses port 80 by default, HTTPS uses port 443.
|
||||||
|
|
||||||
As part of its bigger goal to "encrypt the entire Internet", the [Electronic Frontier Foundation](https://certbot.eff.org/about/) developed Certbot, a free and open source tool for automating the server-side deployment of [Let's Encrypt Certificates](https://letsencrypt.org/), thus enabling HTTPS.
|
As part of its bigger goal to "encrypt the entire Internet", the [Electronic Frontier Foundation](https://certbot.eff.org/about/) developed Certbot, a free and open source tool for automating the server-side deployment of [Let's Encrypt Certificates](https://letsencrypt.org/), thus enabling HTTPS.
|
||||||
|
|
||||||
@ -181,6 +188,96 @@ Run Certbot to get the right certificates for your domain:
|
|||||||
```bash
|
```bash
|
||||||
$ sudo certbot certonly -d myserver.org
|
$ sudo certbot certonly -d myserver.org
|
||||||
```
|
```
|
||||||
|
After following the process, and if all went well, you should now see the following message:
|
||||||
|
|
||||||
|
```
|
||||||
|
- Congratulations! Your certificate and chain have been saved at:
|
||||||
|
/etc/letsencrypt/live/mydomain.org/fullchain.pem
|
||||||
|
Your key file has been saved at:
|
||||||
|
/etc/letsencrypt/live/mydomain.org/privkey.pem
|
||||||
|
Your cert will expire on 2019-09-24. To obtain a new or tweaked
|
||||||
|
version of this certificate in the future, simply run certbot
|
||||||
|
again. To non-interactively renew *all* of your certificates, run
|
||||||
|
"certbot renew"
|
||||||
|
- If you like Certbot, please consider supporting our work by:
|
||||||
|
|
||||||
|
Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
|
||||||
|
Donating to EFF: https://eff.org/donate-le
|
||||||
|
```
|
||||||
|
|
||||||
|
Now, it is time to edit your etc/apache2/sites-available/mydomain.conf file accordingly:
|
||||||
|
|
||||||
|
```
|
||||||
|
<VirtualHost *:80>
|
||||||
|
ServerName mydomain.org
|
||||||
|
|
||||||
|
ServerAdmin webmaster@localhost
|
||||||
|
DocumentRoot /var/www/html
|
||||||
|
|
||||||
|
ErrorLog ${APACHE_LOG_DIR}/mydomain.error.log
|
||||||
|
CustomLog ${APACHE_LOG_DIR}/mydomain.access.log combined
|
||||||
|
</VirtualHost>
|
||||||
|
|
||||||
|
#NEW CONFIG STARTS HERE
|
||||||
|
<IfModule mod_ssl.c>
|
||||||
|
<VirtualHost *:443>
|
||||||
|
ServerName mydomain.org
|
||||||
|
|
||||||
|
ServerAdmin webmaster@localhost
|
||||||
|
DocumentRoot /var/www/html
|
||||||
|
|
||||||
|
ErrorLog ${APACHE_LOG_DIR}/mydomain.error.log
|
||||||
|
CustomLog ${APACHE_LOG_DIR}/mydomain.access.log combined
|
||||||
|
|
||||||
|
SSLEngine on
|
||||||
|
#PATH TO YOUR CERTIFICATES (note: don't forget to replace mydomain.org with your actual domain name!)
|
||||||
|
SSLCertificateFile /etc/letsencrypt/live/mydomain.org/fullchain.pem
|
||||||
|
SSLCertificateKeyFile /etc/letsencrypt/live/mydomain.org/privkey.pem
|
||||||
|
</VirtualHost>
|
||||||
|
</IfModule>
|
||||||
|
```
|
||||||
|
In case you didn't notice, there is now an if statement that evaluates true in case a certain module is present. In this case, it evaluates to true if [mod_ssl](http://www.modssl.org/) is present. [Apache modules](https://en.wikipedia.org/wiki/List_of_Apache_modules) can be installed as following:
|
||||||
|
|
||||||
|
```bash
|
||||||
|
$ sudo a2enmod modulename
|
||||||
|
```
|
||||||
|
To verify which modules are already running on your server, type:
|
||||||
|
|
||||||
|
```bash
|
||||||
|
$ sudo apache2ctl -M
|
||||||
|
```
|
||||||
|
|
||||||
|
If the required ssl_module is not listed, run:
|
||||||
|
|
||||||
|
```bash
|
||||||
|
$ sudo a2enmod ssl
|
||||||
|
```
|
||||||
|
|
||||||
|
Time to restart Apache and load all of these changes!
|
||||||
|
|
||||||
## index.html
|
## index.html
|
||||||
|
|
||||||
|
At this point, when typing https://mydomain.org into your browser, you're greeted with a page that looks a little something like this:
|
||||||
|
|
||||||
|
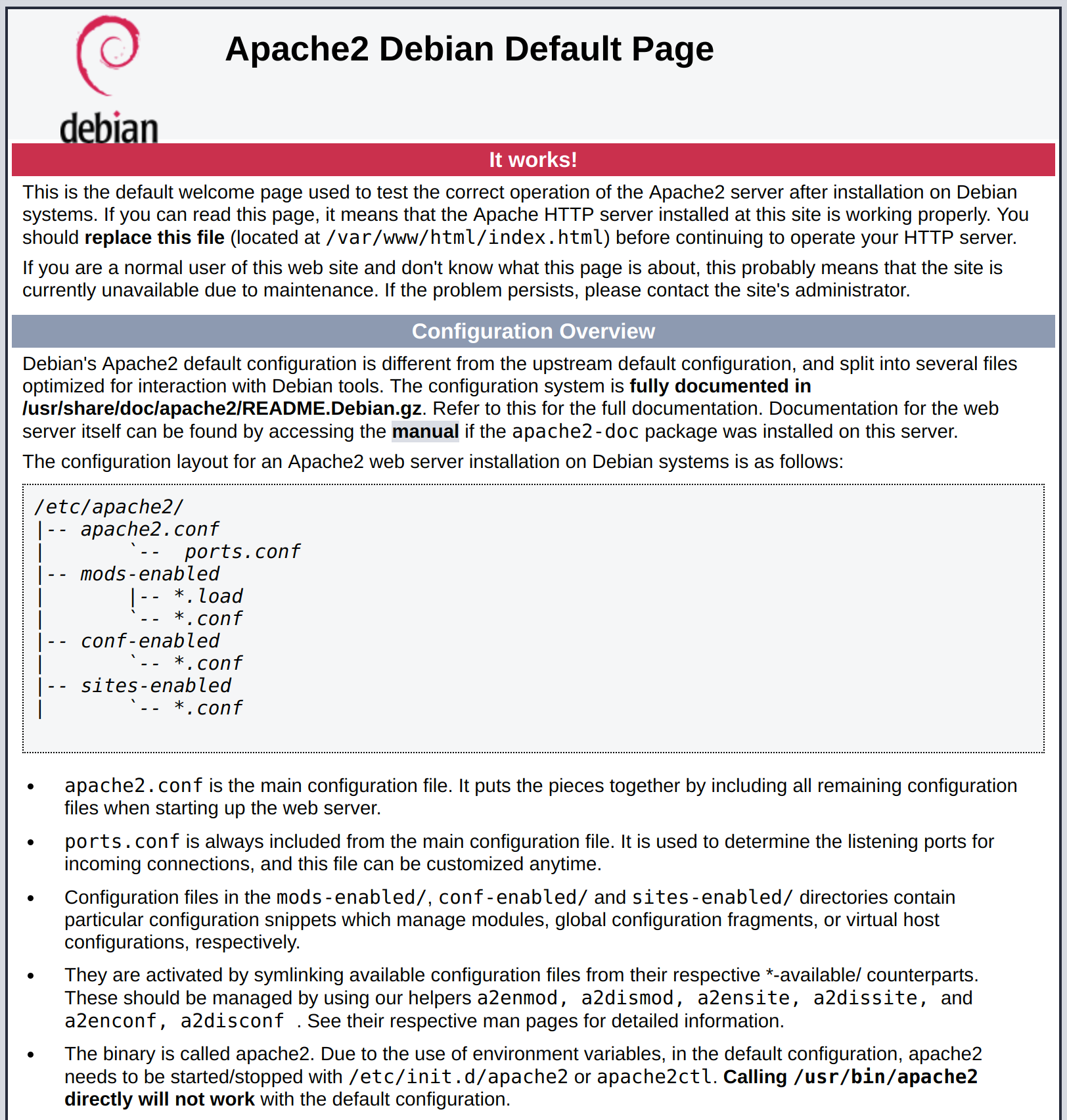
|
||||||
|
|
||||||
|
If you cd into your /var/www/html folder, you will find this default index.html. As recommended by this page itself, you should edit this file before continuing operations on your webserver.
|
||||||
|
Open it on your favourite text editor and let's get started on a bare-bones "Hello Homebrew World"! webpage.
|
||||||
|
|
||||||
|
```html
|
||||||
|
<!doctype html>
|
||||||
|
|
||||||
|
<html lang="en">
|
||||||
|
<head>
|
||||||
|
<meta charset="utf-8">
|
||||||
|
<title>My first homebrewed webpage</title>
|
||||||
|
</head>
|
||||||
|
|
||||||
|
<body>
|
||||||
|
<h1>Hello Homebrew World!</h1>
|
||||||
|
</body>
|
||||||
|
</html>
|
||||||
|
```
|
||||||
|
Open your browser again and savour the fruits of your hard work.
|
||||||
|
|
||||||
|
That was it! Now you are ready to have hours of endless fun sailing the vast sea of HTML, CSS, JavaScript, etc.
|
||||||
|
|||||||
Loading…
Reference in New Issue
Block a user